


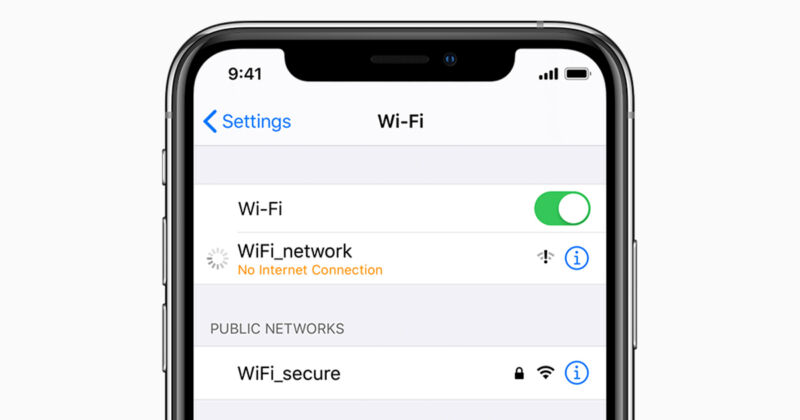
There’s a bug in iOS that disables Wi-Fi connectivity when devices join a network that uses a booby-trapped name, a researcher disclosed over the weekend.
By connecting to a Wi-Fi network that uses the SSID “%p%s%s%s%s%n” (quotation marks not included), iPhones and iPads lose the ability to join that network or any other networks going forward, reverse engineer Carl Schou reported on Twitter.
After joining my personal WiFi with the SSID “%p%s%s%s%s%n”, my iPhone permanently disabled it’s WiFi functionality. Neither rebooting nor changing SSID fixes it :~) pic.twitter.com/2eue90JFu3
— Carl Schou (@vm_call) June 18, 2021
It didn’t take long for trolls to capitalize on the finding:
An absence of malice
Schou, who is the owner of hacking resource Secret Club, initially saw no easy way to restore Wi-Fi capabilities. Eventually, he found that users could reset network functionality by opening Settings > General > Reset > Reset Network Settings.
Apple representatives didn’t respond to emailed questions, including if there were plans to fix the bug and whether it affected macOS or other Apple offerings.
Schou said in an Internet message that the bug is caused by the internal logging functionality in the iOS Wi-Fi daemon, which uses the SSID inside of format expressions. The condition makes it possible in some cases for unauthorized format strings to be injected into sensitive parts of the highly fortified Apple OS. He and other security experts, however, said there was little chance of the bug being exploited maliciously.
“In my opinion, the real-world threat is minimal as you are quite constrained by the length of the SSID and the format expression itself,” he explained. “You could potentially turn this into an information disclosure in the logger, but I do not think it is even remotely possible to get code execution.”
A quick analysis of the bug by an outside researcher agreed that it isn’t likely the bug could be exploited to execute malicious code. The analysis also found that the bug appears to stem from a flaw in an iOS logging component that uses the concat function to effectively convert the SSID string into a format string before writing it to the log file.
Because the strings aren’t echoed to sensitive parts of the iOS, a hacker is unlikely to succeed in abusing the logging feature maliciously. Besides that, an exploit would require a person to actively join a network that contains a suspicious-looking name.
“For the exploitability, it doesn’t echo and the rest of the parameters don’t seem to be controllable,” the researcher wrote. “Thus I don’t think this case is exploitable. After all, to trigger this bug, you need to connect to that WiFi, where the SSID is visible to the victim. A phishing Wi-Fi portal page might as well be more effective.”
But…
Not all researchers reached the same assessment. Researchers from security firm AirEye, for instance, said that the technique could be used to bypass security appliances that sit at the perimeter of a network to block unauthorized data from entering or exiting.
“What we found was that although the latest iPhone Format String flaw is perceived as seemingly benign, the implications of this vulnerability stretch far and beyond any joking matter,” AirEye researcher Amichai Shulman wrote. “If you are responsible for the security of your organization, you should be aware of this vulnerability as a related attack can affect corporate data while bypassing common security controls such as NAC, firewalls and DLP solutions.”
Shulman also said that macOS is affected by the same bug. Ars couldn’t immediately verify this claim. Schou said he hasn’t tested macOS but that others have reported they were unable to reproduce the error on the OS.
The real story
Schou told me that the network crashes don’t happen every time an iOS device connects to a malicious SSID. “It’s nondeterministic, and sometimes you are lucky enough that the Wi-Fi daemon crashes without it persisting the SSID,” he explained. The flaw has existed since at least iOS 14.4.2, which was released in March, and possibly for years before that.
He said he discovered the bug when he connected an iPhone to one of his wireless routers. “All of my devices are named after various injection techniques to mess with old devices that do not sanitize input,” Schou said. “And apparently, the latest iOS.”
The crash is caused by what researchers call a uncontrolled format string bug. The flaw arises when corrupted user input is the format string parameter in certain functions written in C and C-style languages. Use of format tokens such as %s and %x can in some cases print data to memory. The bug was initially considered harmless. More recently, researchers have recognized the potential for writing malicious code using the %n format token.
The most surprising thing about this bug is the fact that it exists at all. A wide assortment of programming guidelines exists for preventing these types of format string flaws. The failure of what’s arguably the world’s most secure consumer OS to adequately implement these techniques in 2021 is the real story here.
