
Join today’s leading executives online at the Data Summit on March 9th. Register here.
Depending on who you ask in the cybersecurity world, there’s a big shift happening right now in the area of application security. The idea is that the process of ensuring that code is secure should not fall only, or even predominantly, to the security team. The developers themselves need to play a leading role.
To actually make that happen in practice, however, developers need tools that are familiar to them and fit into how they work normally. Companies such as Snyk, whose customers include Google and Salesforce, and Data Theorem, which serves Netflix and Microsoft, are among the major players that have taken this approach thus far.
One startup working to join their ranks by taking a developer-focused approach to AppSec is Bright Security, which was formerly known as NeuraLegion. The new name, and a $20 million series A funding round for the company, are both being unveiled today. The round was led by Evolution Equity Partners, and included backing from DNX Ventures, J-ventures, Fusion Fund and Incubate Fund.
Distinct from companies such as Snyk, Bright Security focuses just on dynamic application security testing (DAST) — which involves running scans across the entire software development lifecycle for vulnerabilities from the outside, the way that an attacker would view the application, rather than focusing on examining open source or proprietary code from the inside for security issues.
“Just like Snyk has made a significant change in how people did software composition analysis (SCA) and now static analysis — toward making it much more accessible to developers and making sure that it fits into a modern development environment — this is a complimentary solution on the dynamic analysis front,” said Gadi Bashvitz, cofounder and CEO of Bright Security, in an interview.
Catching vulnerabilities
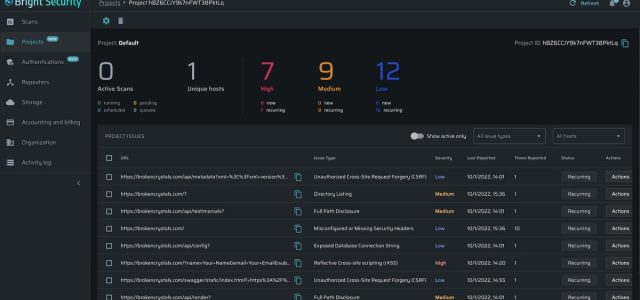
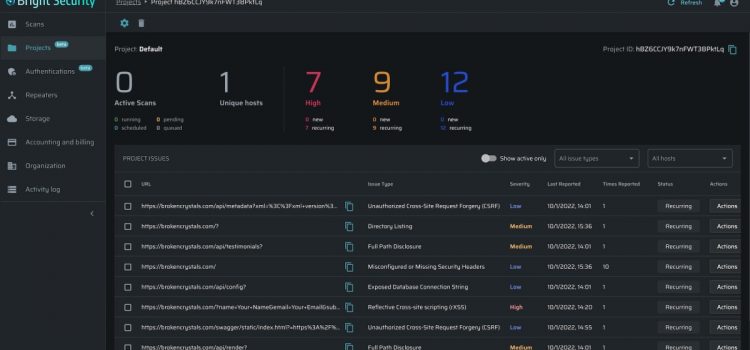
Bright Security is seizing on the opportunity to bring security earlier into the application development process, commonly referred to as “shifting left,” for the DAST side of the AppSec equation. Dynamic analysis, for many organizations today, happens too late in the process — leading most companies to deploy applications into production that still contain vulnerabilities, according to Bright Security.
In fact, according to a report from NTT Application Security, 50% of all web apps were vulnerable to at least one serious exploitable vulnerability throughout 2021.
With Bright Security’s DAST platform for automatically testing all aspects of an application and APIs, the company aims to “make sure that organizations find these vulnerabilities early, and remediate them early before they get into production,” Bashvitz told VentureBeat.
Standard DAST solutions were a good fit for organizations in years past, when new software was getting released every few months and you’d have significant time allocated for testing, he said. But for companies that are now releasing new software updates constantly, that’s a “very different velocity” and not a situation that traditional DAST was created for, according to Bashvitz.
“These legacy solutions were not built to run in a world where you’re doing multiple releases a day, because they took a long time to run,” he said. “And they were targeted at the AppSec team. They weren’t targeted at developers. And the only way in which you can actually meet this velocity, and deploy quickly, is if you target the solutions and make sure that the solutions are convenient for developers to use them.”
Made for developers
And so, this is the way that Bright Security is looking to stand out from other players in the market — by offering a DAST tool that can perform scans quickly enough to keep up with the current pace of software releases, and that is made for use by developers.
“The developer is saying, ‘I need something that will run in 30 seconds at the most,’” Bashvitz said. “Our solution was designed, when it’s integrated into the development process, to run much much faster [than standard DAST], because we are limiting the number of parameters and limiting the number of entry points that we’re testing.”
In terms of making the solution developer-friendly, the Bright Security tool can be used within the continuous integration / continuous delivery (CI/CD) process. That means the developer just sees the tickets have been opened for them in their ticketing system, and addresses any security issues that way.
“Security vulnerabilities are bugs — but for some reason we treat them differently. And we shouldn’t treat them differently,” Bashvitz said. “They’re a bug and they should be dealt with like any other bug. So, tickets should be opened and remediation guidelines should be provided.”
Bright Security can also be used via an integration within unit testing platforms. “Whatever tools the DevOps organization is using in order to drive their development lifecycles, we are integrated with them to make sure that it’s not labor intensive to drive our solutions,” Bashvitz said.
An additional element that makes Bright Security a good fit for developers is the tool’s ability to “present the information to developers in ‘developer speak,’ including remediation guidelines,” he said.
The tool also reduces the “noise” for developers, Bashvitz said. “Because we are DAST, we can actually test if a vulnerability is exploitable or not. And we can remove all the ones that are false positives,” he said.
Ultimately, for thousands or tens of thousands of organizations that are using DAST today, the traditional tools “just don’t fit into what they’re trying to do anymore,” Bashvitz said. “So the big opportunity is making sure that organizations can deploy dynamic analysis in a way that fits their modern development environment.”
Customer traction
Since launching its product commercially in November 2020, Bright Security has landed more than 50 enterprises as customers. Those include ZoomInfo, BDO, Nvidia and PremFina.
Along with selling directly to enterprises, Bright Security also allows developers to sign up themselves and use the product for free. The startup says it now has thousands of developers who are using the product in that way.
Then eventually, that can lead their enterprise to become a customer. About 10% of Bright Security’s customers have come aboard through that means, and “we are expecting that to increase significantly” going forward, Bashvitz said.
With the new funding, the company has raised a total of $25.6 million in funding since its launch in 2018.
Bright Security is now planning to hire for its engineering team as well as its sales and marketing team. The San Francisco-based company, which also has an office in Israel, currently employs 68, and is expecting to surpass 100 by the end of June.
Along with Bashvitz, the other founders of the company are COO Shoham Cohen, CTO Bar Hofesh and CPO Art Linkov. Cohen had previously been serving as CEO — until January, when he was succeeded by Bashvitz, formerly the president and chief customer officer of the company.
Business logic flaws
Apart from addressing technical vulnerabilities, another differentiator for the Bright Security tool is its ability to provide scanning for business logic vulnerabilities. This class of vulnerabilities — which are flaws in the design of the application — enable legitimate use of the application to potentially be exploited.
While it’s been typically assumed that only humans can test for business logic vulnerabilities, Bright Security says it uniquely enables automated scanning for such flaws using AI.
Whatever type of vulnerability it is, catching flaws early has a big payoff for organizations — not just in terms of lowering their security risk, but also in terms of productivity, according to Bashvitz. It’s significantly easier to remediate an issue that is found as part of the build process, than it is to remediate the issue if it’s already in production, he said.
After an app is in production, the developer needs to go back into the code and re-familiarize themself with everything all over again, Bashvitz said. “It’s much more efficient to solve these vulnerabilities early in the cycle. And that’s exactly what we enable organizations to do.”
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Learn More
